Password Replacement: Your Face Here
Jean-Luc Jackson | July 7, 2022
Biometrics promise convenient and secure logins, making passwords a thing of the past. However, consumers should be aware of possible gaps in security and vigilant of long-term shifts in cultural norms.
Technology leaders such as Microsoft, Apple, and Google are promising an impending future free of passwords. Passwordless authentication methods in use today include text or in-app validation codes, emailed “magic links”, or the user’s biometric data. These biometric-based methods are poised to replace traditional passwords and become the primary authentication systems for users’ big tech. Biometric authentication methods are no longer confined to spy films, consumers can now prove their digital identities using facial and fingerprint scans instead of employing their favorite password management service. These are exciting developments, but consumers should always be wary when exposing sensitive personal information like biometrics. The stakes with biometric data insecurity are high: passwords can be reset, new credit cards can be printed, but biometrics are permanently tied to and identifiable of their source.
The National Academy of Sciences defines biometrics as “the automated recognition of individuals based on their behavioral and biological characteristics [1].” Biometrics take advantage of features that are unique to individuals and that don’t change significantly over time. Commonly encountered examples include a person’s fingerprints, face geometry, voice, and signature. Other contenders include a person’s gait, heartbeat, keystroke dynamics, and ear shape. In other words, the way you walk, your typing patterns, and the contours of your ears are distinctive and could be used to identify you.
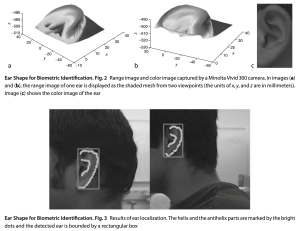
The advantage of biometrics in authentication is that they cannot be forgotten or guessed, and they are convenient to present. Microsoft announced in 2021 that consumers could get rid of their account passwords and opt-in to using facial recognition or fingerprint scanning (a service dubbed “Windows Hello”) [2]. Apple and Google have also announced similar biometric passkey technologies to be rolled out later this year [3, 4]. With this momentum, biometrics will soon be ubiquitous across modern smart devices and could one day be the only accepted login method.
Passwordless technologies offered by these tech companies utilize de-centralized security standards like FIDO (Fast IDentification Online). This authentication process involves a pair of public and private keys. The public key is stored remotely on a service’s database while the private key is stored on the user’s device (e.g., a smart phone). When the user proves their identity on their device using biometrics (e.g., with a face scan), the private key is sent to the online service and the login is approved when matched to the remote public key. This design ensures that biometric information remains on the device and is never shared or stored on a server, eliminating the threats of interception or database breaches.
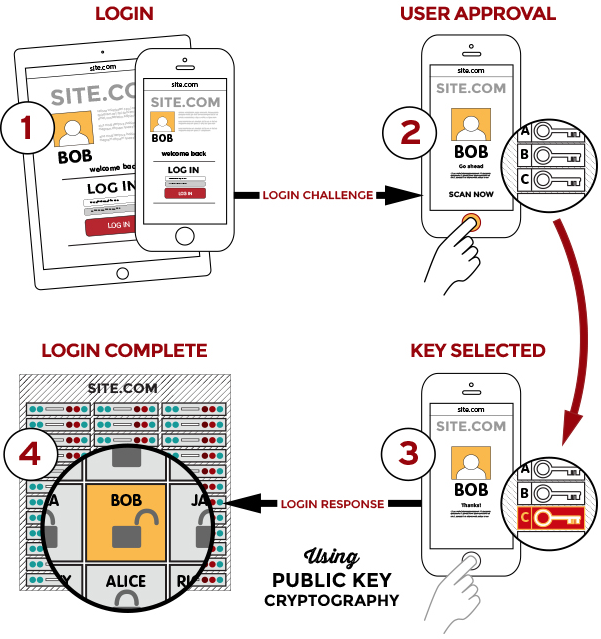
FIDO standards are an example of a de-centralized authentication system since biometric data is verified on-device and is not stored on a central server. A centralized system, on the other hand, authenticates by comparing biometric data to data saved in a central database. These systems are prone to manipulation and data breaches because of the higher potential for attacks. We should be vigilant of organizations that use centralized systems and pay close attention when they are used in government applications, such as storing biometric data about their citizens [5].
Though passwordless methods minimize security risks, gaps do exist. Researchers successfully reconstructed people’s original face images using their on-device data that result from facial recognition scans [6]. The potential to decode numerical representations of biometric data poses the threat of a new form of identity theft. Since biometrics are treated as ground-truth authentication, such a theft would provide a variety of access in a world filled with biometric logins. While most thieves won’t be able to utilize stolen biometric data with off-the-shelf methods, as technology evolves this risk will continue to expand and should receive additional attention.
It’s also possible to create imitation biometrics that allow unwanted access. Fingerprint security has often been bypassed by reproducing a copy of a fingerprint, but a group of researchers in 2018 created a machine learning model that generated fake fingerprints that successfully gained access to smart phones [7]. The continuous advancement of technology yields both benefits and risks depending on who has the tools, reminding us to exercise caution in sharing data and pushing companies to keep consumer protection as a priority.
There is no doubt that biometrics offer added convenience, and the latest authentication standards promise stronger levels of security. But as biometrics become the prevailing authentication method, we normalize the routine use of sensitive personal information in a variety of contexts. Individuals will inevitably grow more accustomed to sharing valuable information with organizations to remain productive members of society. Moving forward, it will be even more important for us as consumers to demand transparency and hold organizations accountable to minimizing data collection to only what is necessary and not using data for secondary purposes.
For context, there is currently no federal regulation regarding biometric privacy. Various states have enacted biometric-specific privacy laws, with Illinois and California leading the way in protecting its citizens. The number of state laws continues to grow, signaling the potential for national regulation soon.
Citations
[1] https://www.ncbi.nlm.nih.gov/books/NBK219892/
[2] https://www.microsoft.com/security/blog/2021/09/15/the-passwordless-future-is-here-for-your-microsoft-account/
[3] https://developer.apple.com/passkeys/
[4] https://developers.google.com/identity/fido
[5] https://www.technologyreview.com/2020/08/19/1007094/brazil-bolsonaro-data-privacy-cadastro-base/
[6] https://ieeexplore.ieee.org/document/8338413
[7] https://www.wired.com/story/deepmasterprints-fake-fingerprints-machine-learning/
Images
[1] https://www.microsoft.com/en-us/security/business/identity-access/azure-active-directory-passwordless-authentication
[2] https://link.springer.com/referenceworkentry/10.1007/978-1-4419-5906-5_738
[3] https://fidoalliance.org/how-fido-works/
