In a Digital Playground, Who Has Access To Our Children?
By Anonymous | October 27, 2022
On one particularly lazy Saturday afternoon, I heard my then-8 year old daughter call, “Hey dad! Someone’s talking to me on my iPad. Can I talk back?” Taking a look, I was curious to see that another unknown user’s avatar was initiating a freeform text chat in a popular educational app. I didn’t realize it even had a chat feature. My dad-spidey-sense kicked in and I asked my daughter what she thought. She replied, “I don’t know this person, they’re a stranger, I’ll block them.”
![]()
Source: https://www.adventureacademy.com
Most parents these days have a good general idea about how to moderate “pull content” (where users choose content to retrieve) for their kids as they use net-connected tablets at home, but for me this situation represents a different kind of concern — “how apps may allow the public at large access to communicate live and directly, and at any time, with our kids at home without our knowledge, either through text-based chat, or more concerning, video or audio.
Solove’s Privacy Taxonomy
In 2006, privacy law professor Daniel Solove published a taxonomy to help illustrate harms from privacy violations, modeled across a complete lifecycle flowing from information collection, to processing and dissemination, to invasion. My concern lies in “intrusion” within the invasion stage, which he describes as “invasive acts that disturb one’s tranquility or solitude”.
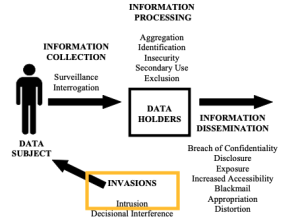
Source: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=667622
This intrusion makes children, already vulnerable due to lack of maturity and autonomy, even more vulnerable to a myriad of both online and physical harms, such as scams, phishing attacks, child predation, kidnapping, cyberbullying, and identity theft.
Fourth Amendment Rights
The Fourth Amendment constitutionally protects, “The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures”. The framers of the constitution, of course, didn’t have the Internet in mind in the 18th century, however a landmark case in 1967, Katz v. United States extended the interpretation of the Fourth Amendment to locations where a person would have a “reasonable expectation of privacy I would argue that the right to defend one’s household, and family within, from such intrusion would apply to the digital realm also.
Cleveland State University’s Online Test Practices
A recent example of the Fourth Amendment being applied within the digital realm involves a ruling by a federal judge against Cleveland State University. While administering a remote online test to student Aaron Ogletree, the university required Aaron to provide test proctors with live webcam footage of a wide scanning view of his bedroom. The judge ruled that the university violated Aaron’s constitutional right against unreasonable search and seizure due Aaron’s lack of choice on the matter. Similarly, younger kids subjected to invasive app access by default may not know how to prevent this access.
Children’s Online Privacy Protection Act (COPPA)
The COPPA rule became effective in 2020, in order to further protect the online privacy of children under the age of 13 by requiring verifiable parental consent (VPC) before any collection of personally identifiable information (PII) can take place. Enforced primarily by the FTC, this legislation is important in providing parents with a basic standard of protection and a workflow to proactively opt in and control the online experience. Despite the best efforts of app developers to follow COPPA and build safe communities, anyone could still be on the other end of unsolicited communication if bad actors falsify sign-up information or if accounts get hacked.
Internet Crimes Against Children Task Force
In 1998, the Office of Juvenile Justice and Delinquency Prevention (OJJDP) created the Internet Crimes Against Children Task Force Program (ICAC), in part due to “heightened online activity by predators seeking unsupervised contact with potential underage victims”. Their website shares, “Since 1998, ICAC Task Forces have reviewed more than 1,452,040 reports of online child exploitation, resulting in the arrest of more than 123,790 suspects.”
Conclusion
Fast forward to today, my younger child is now 6 and has asked for the same educational app. I’ve done enough due diligence to be comfortable installing it for him, but only because the app gives us the option to fully disable the “push chat” feature until he’s old enough to safely use it. If he’s like his older sister, he’ll outgrow the educational content well before then.

Source: https://pbs.twimg.com/media/FSV4TiPWYAEdWXx?format=jpg
References
[1] https://www.techopedia.com/definition/21548/push-media
[2] https://constitution.congress.gov/constitution/amendment-4/
[3] https://www.pewresearch.org/internet/2020/07/28/parenting-approaches-and-concerns-related-to-digital-devices/
[4] https://ssrn.com/abstract=667622
[5] https://www.americanbar.org/groups/judicial/publications/judges_journal/2016/spring/telephone_technology_versus_the_fourth_amendment/
[6] https://www.law.cornell.edu/constitution-conan/amendment-4/fourth-amendment-historical-background
[7] https://www.theverge.com/2022/8/23/23318067/cleveland-state-university-online-proctoring-decision-room-scan
[8] https://fpf.org/verifiable-parental-consent-the-state-of-play/
[9] https://ojjdp.ojp.gov/programs/internet-crimes-against-children-task-force-program
