The Physics Behind Good Data Security
By Rani Fields
The data security apocalypse is upon us. While that statement might be a bit hyperbolic, 2017 and 2018 were certainly emblematic years in data security. From Panera to Facebook, Aadhaar to Saks Fifth Avenue, the frequency, intensity, and expansiveness of data breaches entered an upward swing with increasing intensity. When you factor in the expensive nature of a breach, at $148 per record (IBM, 2018), the damages from a data breach impacting even a small group can reach into the millions. A company’s ability to quickly respond in a manner which satisfies regulatory officials and placates embroiled public sentiments also increases in complexity as a company’s profile increases. Needless to say, modern companies with an online presence should not concentrate solely on preventing breaches but rather have an extensive focus on managing the fall-out of data breaches. Data breaches should be considered inevitable in today’s world, after all.
Where Proactive Approaches Fail
All companies with a sizeable online footprint should be prepared for a security breach. As penetration methods and social engineering methods become increasingly refined, we cannot reasonably assume any infrastructure to be sufficiently free from the risk of a breach. As such, breaches are a question of when they will occur, not if they will occur. The sources of a breach are varied- they can happen via data leaks, infrastructure hackings and other technical vulnerabilities, phishing and other social engineering methods, and via inside jobs. Because the perfect system and the perfect policy does not exist, a company can always consider themselves vulnerable to some degree along one or more of these axes. Thus, any robust breach policy should be designed to not just mitigate risks but also properly prepare the company for a speedy response in line with which systems were breached and the nature of the resulting exposure.
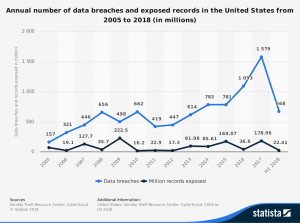
Image via Statista, see references
Technical and Policy Risk Management
As the major attack medium in question is ultimately electronic, we can consider a number of digital areas when reducing risk. Naturally, existing best practices will prevail first and foremost. Identity management, security-by-design, intruder detection, and other similar techniques and technologies should be used wherever possible. The issue with these proactive methods is, with time, the number of resources required to manage a company’s electronic systems can eclipse the benefit hardening these systems can provide as a company’s technical offerings grow.
From a technical standpoint, proactive security policies present a definite amount of benefit, albeit with a limit. Thus, when managing system risk, companies should consider the amount of time and resources required to harden mission-critical systems versus other systems when pursuing a proactive approach.
With a reactive approach to security, we pivot from a question of where we can minimize risk to a question of how we can better understand and respond to security incidents. In this, we see a disproportionate importance in maintaining business continuity plans and disaster recovery plans. For each type of data stored and for each type of breach, you need to ask yourself if your company or group has a clear policy defining:
1. What happens to affected systems in the immediate aftermath of a breach?
2. Can you operate with reduced resources if a system is taken offline due to a breach?
3. Do you have any way to determine which resources were accessed within hours after a breach?
4. Do you have a data protection officer?
5. Does your plan account for any legal and regulatory questions which can occur in the aftermath of a breach, within reason?
Finally, consider modeling privacy and internal data flows when designing data-oriented privacy policies. The key focus of a company in the wake of a breach will be a fast and accurate response; knowing which entities had their data exposed and which specific data were affected are critical to ensuring that your company takes the correct response at the correct time. Furthermore, knowing this information in a process-oriented manner opens pathways to efficiently reducing risk by way of reducing attack surfaces while enabling internal security policies to operate smoothly.
Due to both evolving regulatory changes and the ever-evolving security landscape, the failure to be able to act in a reactive fashion can damage a company more than the benefit provided by simply reducing the risk of a breach. Thus, companies and stakeholders should review their policies to ensure procedures are properly defined so that a company can act in a reactive fashion when the time inevitably comes.

See also:
1. Cost of a Data Breach Study. (2018). Retrieved from https://www.ibm.com/security/data-breach
2. U.S. data breaches and exposed records 2018 | Statistic. (2018). Retrieved from https://www.statista.com/statistics/273550/data-breaches-recorded-in-the-united-states-by-number-of-breaches-and-records-exposed/
3. Data Breach Reports (Tech.). (2018, June 30). Retrieved https://www.idtheftcenter.org/wp-content/uploads/2018/07/DataBreachReport_2018.pdf
4. The History of Data Breaches. (2018, November 07). Retrieved from https://digitalguardian.com/blog/history-data-breaches
5. Data Breach Notification Requirements Coming from EU Expand Obligations for Organizations Worldwide. (2017, September 21). Retrieved from https://www.mayerbrown.com/data-breach-notification-requirements-coming-from-eu-expand-obligations-for-organizations-worldwide/
Images from:
1. University of West Florida. (n.d.). Legal & Consumer Info. Retrieved from https://uwf.edu/go/legal-and-consumer-info/general-data-protection-regulation-gdpr/
2. U.S. data breaches and exposed records 2018 | Statistic. (2018). Retrieved from https://www.statista.com/statistics/273550/data-breaches-recorded-in-the-united-states-by-number-of-breaches-and-records-exposed/
